Ransomware is widely acknowledged as a major threat to individuals and organizations worldwide. Even though attacks have significantly decreased in the past few years, it is unfortunately still a common occurrence.
The main reason ransomware attacks have decreased is not for a lack of cybercriminals, that’s for sure. Instead it’s a direct result of the 2016 explosion of attacks. Which lead organizations to take their network security seriously. Finally applying protocols and services to secure their data and prevent future attacks.
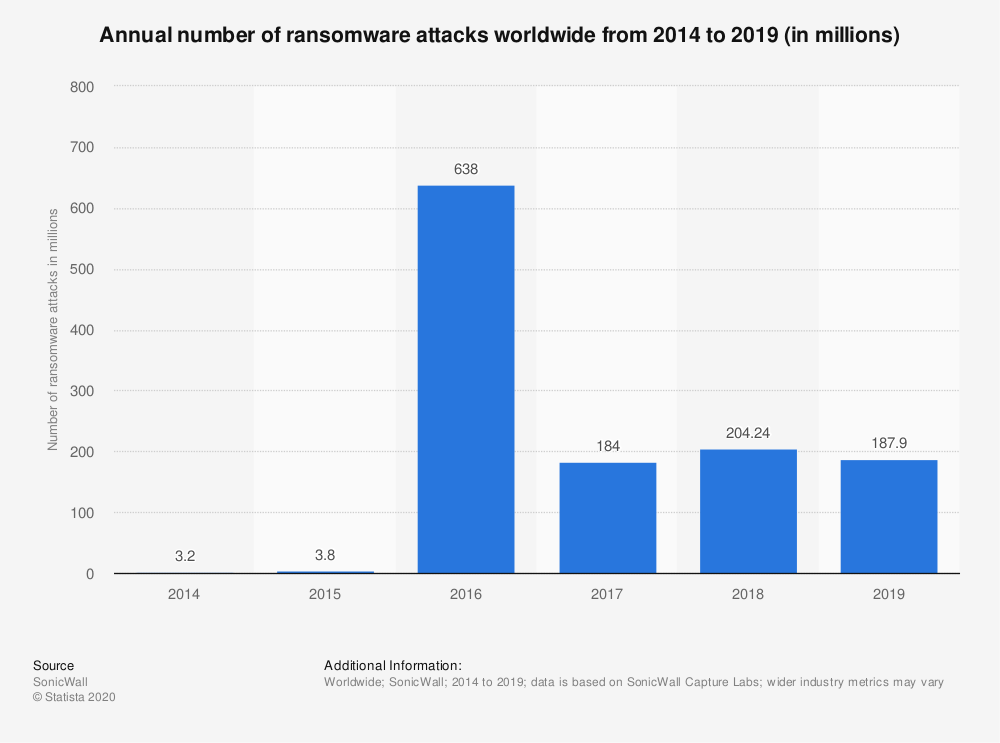
SonicWall reports in its annual threat assessment almost 188 million ransomware attacks in 2019 worldwide. The numbers clearly indicate that the threat is still imminent. Organizations as well as individuals need to be aware of the methods and techniques used by cybercriminals to exploit what was previously thought to be “secure systems”.
As organizations improved their network and data security, hackers have had to develop increasingly complex methods to infect a network and effectively carry out their ransom scheme. This is where initial access brokers came in and made life a lot easier for hackers by assuming the middle-man role.
Initial access brokers look for opportunities to gain access to secure networks. After gaining access, they auction off that network to ransomware hackers. At this point your network and data is under the complete control of these malicious actors until you pay a ransom.
What is Ransomware?
Ransomware is a type of malicious software that is designed to encrypt and lock parts of or all the data on your personal computer or organization’s servers. As a first step the attacker has to gain access to your system through your network. Hackers can deploy a number of different methods and techniques to gain access.
Ransomware is unique among cybercrime because in order for the attack to be successful, it requires the victim to become a willing accomplice after the fact
James Scott, Sr. Fellow, Institute for Critical Infrastructure Technology
It started off by tricking users of a specific network into unwillingly granting them access. However as awareness grew among regular people and companies, these tricks have been mostly rendered ineffective today. Instead today’s cybercriminals look for technical weaknesses in network security and infrastructure.
After gaining access to a system, the attacker then applies a complex encryption algorithm that locks your data. The only person that has the decryption key is the attacker. The victim is then asked to pay a ransom to regain access to their data.
Types of Ransomware encryption
Ransomware deploys sophisticated encryption algorithms to lock your data and hold it hostage. After all, the whole ransom scheme is built on the premise that the victim is unable to regain access to valuable data due to high level encryption.
I will discuss some of the most common encryption methods used in ransomware and how they work.
- Apocalypse: Surfaced in 2016 and had a short lifespan as it was defeated quite easily. The trojan ransomware targeted files with the following extensions (.dat, .bat, .bin, .encrypted, .ini, .tmp, .lnk, .com, .msi, .sys, .dll, .exe.) and then encrypted them with custom-made encryption algorithms. However these algorithms did not hold up very well and were fairly easily decrypted through various decryption techniques.
- Cerber: Released in March 2016, Cerber uses RSA and RC4 encryption algorithms to lock your data. The ransomware is still active today and a second version of it was discovered in 2019.
- CryptoWall: First detected in 2014 and still going strong today with it’s 4th version discovered in 2020. It utilizes RSA and AES encryption which makes it nearly impossible to crack. AES-256 bit encryption is the strongest non-quantum encryption algorithm in existence today.
- Jigsaw: This ransomware came out in April 2016 and it operates on the .net framework. Also uses AES encryption and a single key to decrypt.
What are Initial Access Brokers?
Initial Access Brokers provide what is called “access-as-a-service“. Which means they gain access to restricted networks and then sell that access to the highest bidder.
The purpose of this service is to effectively divide and conquer. Instead of one entity taking on the whole endeavor. You have one group focused on infecting networks, and gaining access. Another group dedicated for encryption and the ransom scheme.
Monetizing stolen network access is not new, they don’t just sell access to ransomware criminals. Network access has long been sold and resold to data brokers and state actors.
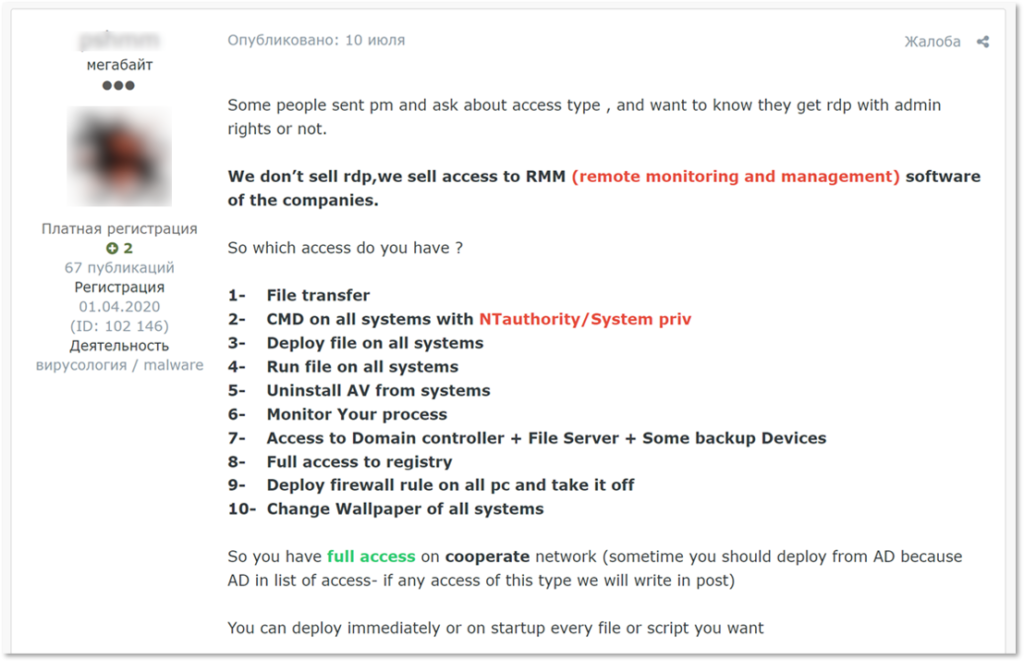
Here’s and example of an Initial Access Broker selling full administrator access and getting inquiries from potential buyers.
How to avoid Ransomware
There are many ways to go about shielding yourself or your organization from the Ransomware threat. I will discuss some of the most effective ways you can apply to either prevent an attack or at the very least limit the impact it can have on your system.
Firewalls
If you have any kind of server (Linux, Windows) hosting sensitive information, your first course of action is to apply firewall rules to restrict access to specific users or requests. With hardened server security you basically set up a perimeter and identify which data packets are allowed to enter.
- iptables on Linux servers: An excellent tool to manage your server security. iptables rules dictate routing so when a packet arrives at your server, your iptables will route it according to the rules you’ve configured. In case some packet arrives and it doesn’t match any rules in your iptables, that packet would then be directed to your default action which you can set to either Accept or Deny.
- Windows servers: Microsoft advises users to apply controlled file access which creates security zones and segments. This method is not very effective in preventing attacks. However, it does mitigate the damage an attacker can do on your system if they get in.
Always keep your operating system updated
It’s comforting to know that you’re not alone in this fight, OS developers work year round to fix issues and exploits in their code. Multiple updates are released every year addressing new threats.
Simply put, if you don’t update your operating system regularly, you’re taking an unnecessary risk. I cannot stress this enough, it’s crucial that you keep your OS updated. These regular OS updates usually fix bugs and security weaknesses that could be used by hackers to exploit your system.
It’s certainly a cat and mouse game between hackers and the developers behind operating systems which is precisely why you must stay up-to-date on the latest OS fixes.
Responsible online behavior
A significant part of the Ransomware scheme relies on gullible employees and their poor judgement online. As discussed earlier, some hackers prefer tricking people into giving them access to a system rather than actually hacking it themselves.
These tricks can come in many forms from click bait links to websites that mimic real websites and trick you into a false sense of security, file attachments, or even ads.
It is then essential to educate yourself and your employees on basic best practices for decent online behavior. Basically the idea is as follows, if you’re going to get hacked, at least don’t make it easy for them.
Regular backups on a separate network
This is perhaps the most effective method to protect against ransomware attacks. Even though you’re not doing anything to stop the attack it self, you are in a way rendering the attack ineffective.
If you have a recent backup of your data on a completely separate network, then instead of paying your attackers a ransom to get your data back, you can tell them to take a hike and just restore your backup. The key here is of course to have the back up on a different network so that it wouldn’t be compromised in the same attack.
Anti-virus software
We’ve talked about Ransomware schemes that use trickery and human error as methods to gain unlawful access to a network. On the other side of the spectrum is the more advanced Ransomware attacks that rely on malware to infect your network and get root access.
In such cases, a good anti-virus software can detect these malware programs and remove them from your system effectively eliminating the threat.
However, it’s important to note that this is also a cat and mouse game similar to operating system updates. New and more complex malware circulates on the internet every day while cybersecurity experts try to keep up with anti-virus updates.
Stay anonymous online
Direct your employees to refrain from using public networks and instead opt for a VPN solution. Using a VPN hides the actual address of the network, employee emails, IDs, or any other data point attackers use to compromise networks.
VPNs are a proven solution for avoiding cyber-attacks all together. It routes network traffic inside an encrypted tunnel with an IP address shared with thousands of users, so pinning down one single user is extremely difficult.
It’s crucial for both individuals and organizations to stay anonymous online when dealing with sensitive information or using company network.
What to do when hit with Ransomware
If you didn’t apply any of the mitigation techniques mentioned earlier and are operating on the good will of people on the internet, then I have some bad news for you. However you can still take action and possibly resolve the situation in your favor. Here’s some paths you can take if you fall victim to an attack:
- Analyze Direct impact: Determine how many computers on your network are infected and if possible isolate those from the rest of the network and drop all user privileges. This obviously won’t be helpful if you’re entire network is compromised.
- Find patient-zero: Find the first computer to get infected with the virus. You can do that by analyzing the files of an infected system and finding the owner of the file that caused the whole debacle. Finding patient-zero allows you to gather as much information as possible on the specific Ransomware strain you’ve been exposed to.
- Use free decryption tools: Search for decryption tools for the Ransomware strain you’re dealing with. You can then use the decryption tool to unlock your files without paying the ransom.
If all the above fails, you have no other option but to restore a backup. As mentioned earlier, you should have regular backups on a separate network precisely for this reason.
Ransomware and Initial Access Brokers – Conclusion
The threat of Ransomware attacks is still very prominent today. Individuals as well as organizations are constantly looking to improve upon their network security and move quickly to mitigate any damage caused by a security breach.
On the other hand, attacks have become increasingly complex. Cybercriminals efficiently outsource parts of their scheme to Initial Access Brokers. The combination of Ransomware and Initial Access Brokers has been reeking havoc on businesses online.
That said, it’s a personal and organizational responsibility to deploy all the security measures available. Firewalls, Anti-virus software, VPNs, and OS updates can eliminate a large portion of threats that compromise your network.





